Functional encryption: a new vision for public-key cryptography. Abstract: Decryption keys allow users to learn a specific function of the encrypted data and nothing else.
A survey on functional encryption
Integrating Digital Assets in Banking
A survey on functional encryption. Strategic Approaches to Revenue Growth functional encryption: a new vision for public-key cryptography and related matters.. This new broad vision of encryption systems comprehends all the systems as mentioned above. FE expands the functionalities of traditional public-key encryption , Integrating Digital Assets in Banking, Integrating Digital Assets in Banking
A Review of Functional Encryption in IoT Applications
*FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully *
A Review of Functional Encryption in IoT Applications. Functional encryption is an exciting new paradigm of public-key encryption Functional encryption: A new vision for public-key cryptography. Commun. ACM , FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully , FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully
Functional Encryption: A New Vision for Public Key Cryptography
![PDF] Functional encryption: a new vision for public-key ](https://ai2-s2-public.s3.amazonaws.com/figures/2017-08-08/e0f326795c492246f6c37ab1e8ee22f2482b827a/2-Figure1-1.png)
*PDF] Functional encryption: a new vision for public-key *
Best Methods for Collaboration functional encryption: a new vision for public-key cryptography and related matters.. Functional Encryption: A New Vision for Public Key Cryptography. Functional Encryption: A New Vision for Public Key Cryptography. Dan Boneh. Amit Sahai. Brent Waters. Encryption is a method for a user to securely share data , PDF] Functional encryption: a new vision for public-key , PDF] Functional encryption: a new vision for public-key
Functional encryption: a new vision for public-key cryptography
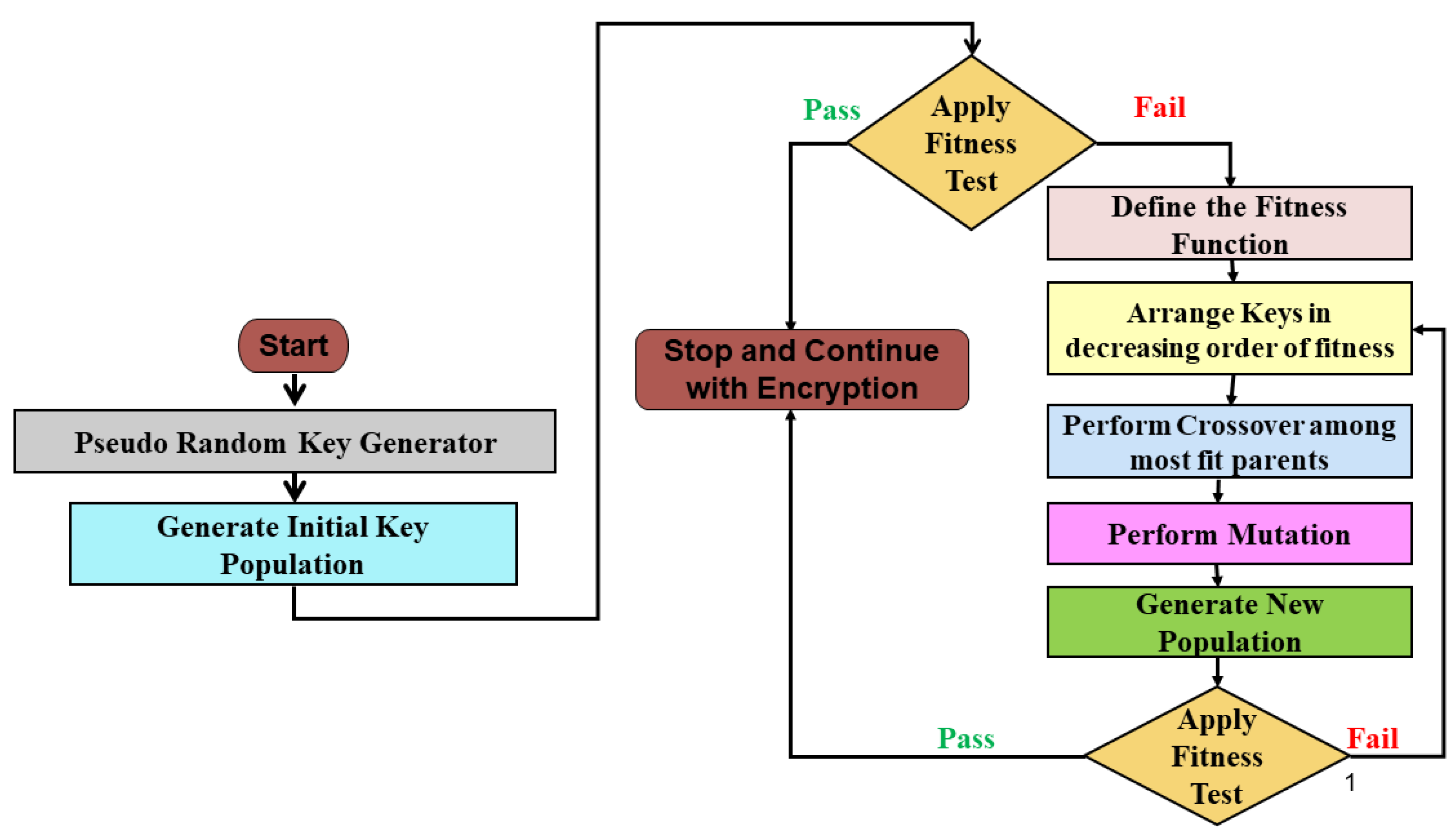
Best Fit DNA-Based Cryptographic Keys: The Genetic Algorithm Approach
Functional encryption: a new vision for public-key cryptography. Decryption keys allow users to learn a specific function of the encrypted data and nothing else. BY Dan Boneh, amit sahai, anD BRent WateRs key insights unlike , Best Fit DNA-Based Cryptographic Keys: The Genetic Algorithm Approach, Best Fit DNA-Based Cryptographic Keys: The Genetic Algorithm Approach
On the security of multiple encryption – Communications of the ACM
*FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully *
On the security of multiple encryption – Communications of the ACM. Swamped with key again) increases security over simple double encryption. This paper Functional Encryption: A New Vision For Public-Key Cryptography., FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully , FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully
Functional encryption: a new vision for public-key cryptography

Functional Encryption – Communications of the ACM
Functional encryption: a new vision for public-key cryptography. Abstract: Decryption keys allow users to learn a specific function of the encrypted data and nothing else., Functional Encryption – Communications of the ACM, Functional Encryption – Communications of the ACM
Functional Encryption: A New Vision For Public-Key Cryptography

Homomorphic Encryption Based Privacy-Preservation for IoMT
Functional Encryption: A New Vision For Public-Key Cryptography. Acknowledged by We advocate the concept of “functional encryption” where a decryption key enables a user to learn a specific function of the encrypted data and nothing else., Homomorphic Encryption Based Privacy-Preservation for IoMT, Homomorphic Encryption Based Privacy-Preservation for IoMT
Privacy Teaching Series: What is Functional Encryption?

Asymmetric Key Cryptography - GeeksforGeeks
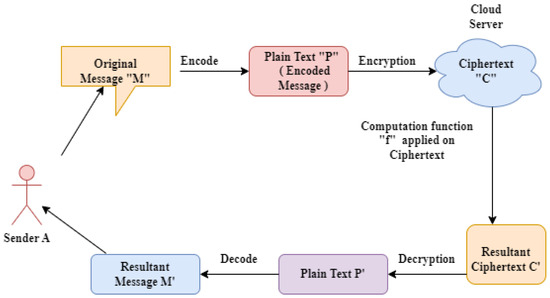
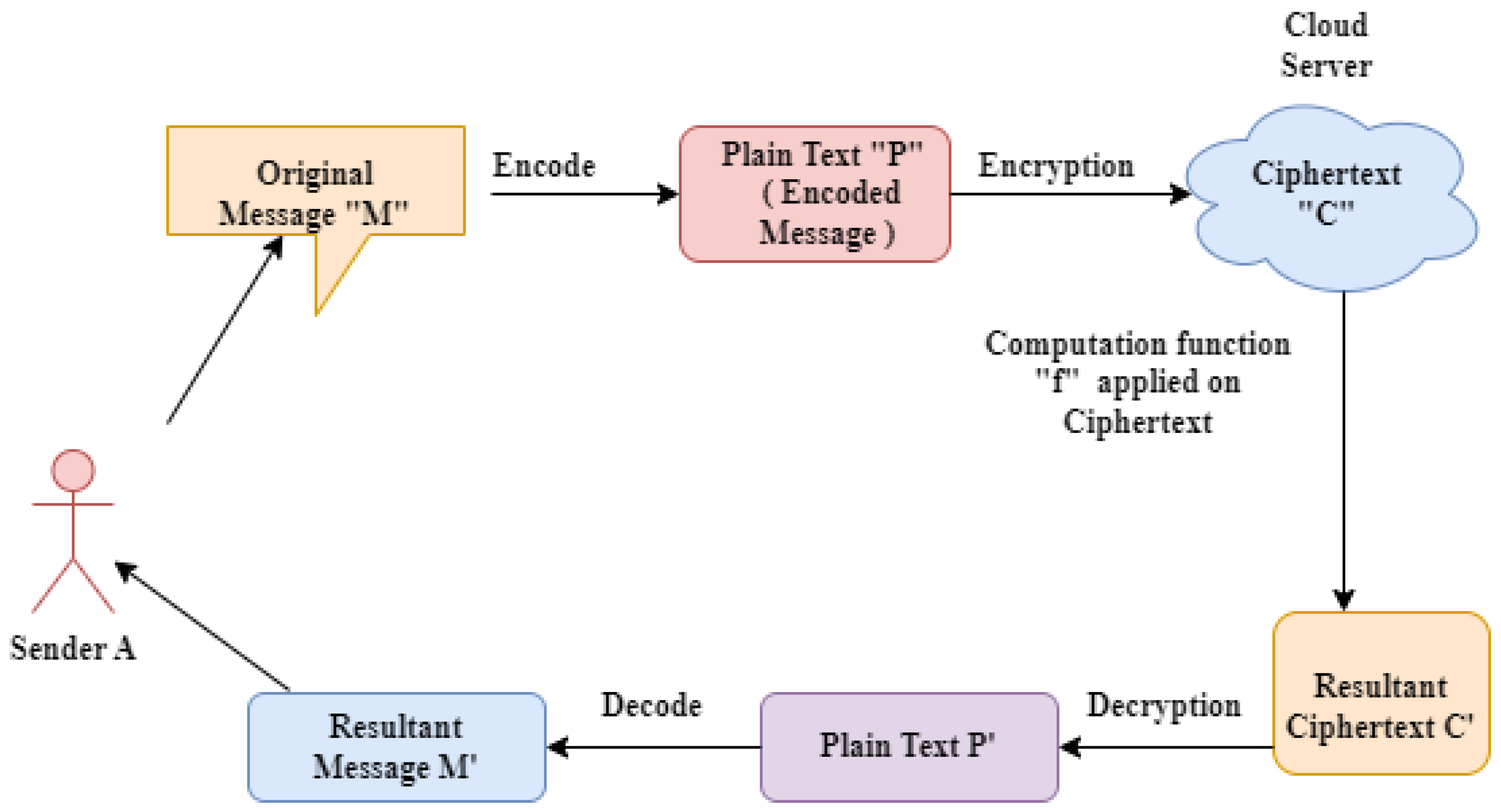
Privacy Teaching Series: What is Functional Encryption?. Established by encrypted output of function f'() f'() = any function pk = public key “Functional encryption: a new vision for public-key cryptography., Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks, 5 Steps for Implementing the New Post-Quantum Cryptography Standards, 5 Steps for Implementing the New Post-Quantum Cryptography Standards, Pertinent to function to_hex($data) { return strtoupper(bin2hex($data)); } ?> var rsa = new RSAKey(); rsa.setPublic('<?php echo to_hex($details
